Talentech ID Single Sign On with OIDC
Consider using the Azure AD Marketplace App
If you are using Azure AD, you should consider using our pre-defined Azure marketplace app when configuring SSO.
This page describes how to configure your Azure AD to support Single SignOn to our Talent Platform using OpenID Connect (OIDC).
Our identity platform, Talentech ID, supports Single SignOn via OpenID Connect. This guide describes how this can be configured in your Azure AD. To get started, you need to contact us in order to configure your system for Single SignOn. You will then get a URL from us to enter in your Azure AD configuration. Then you need to provide us the ClientId and endpoint URL before you are ready to go.
Step by step
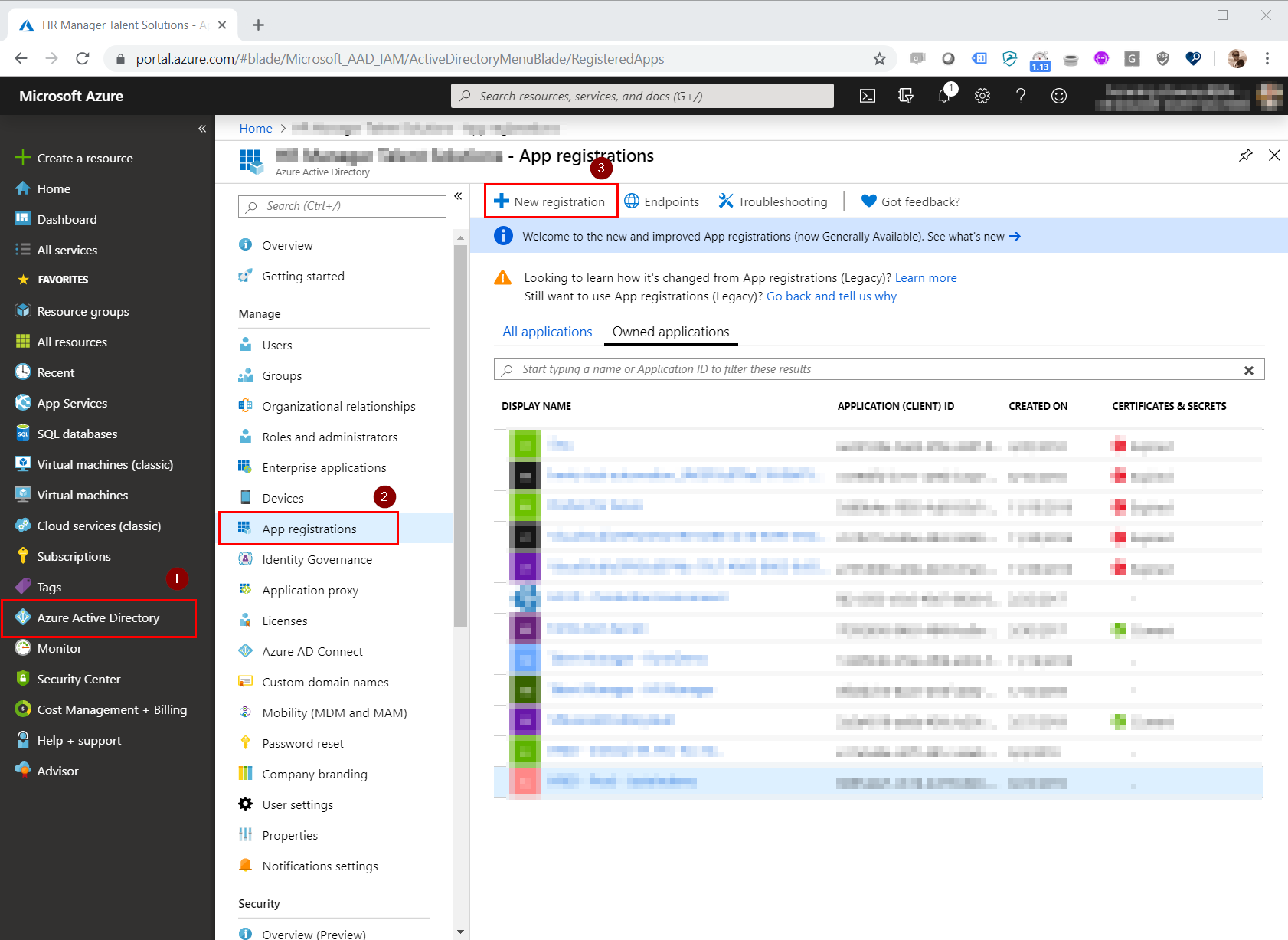
1. Create a new Azure AD App registration
Open the Azure portal and navigate to your Azure Active Directory (1) and click New Registration (2).
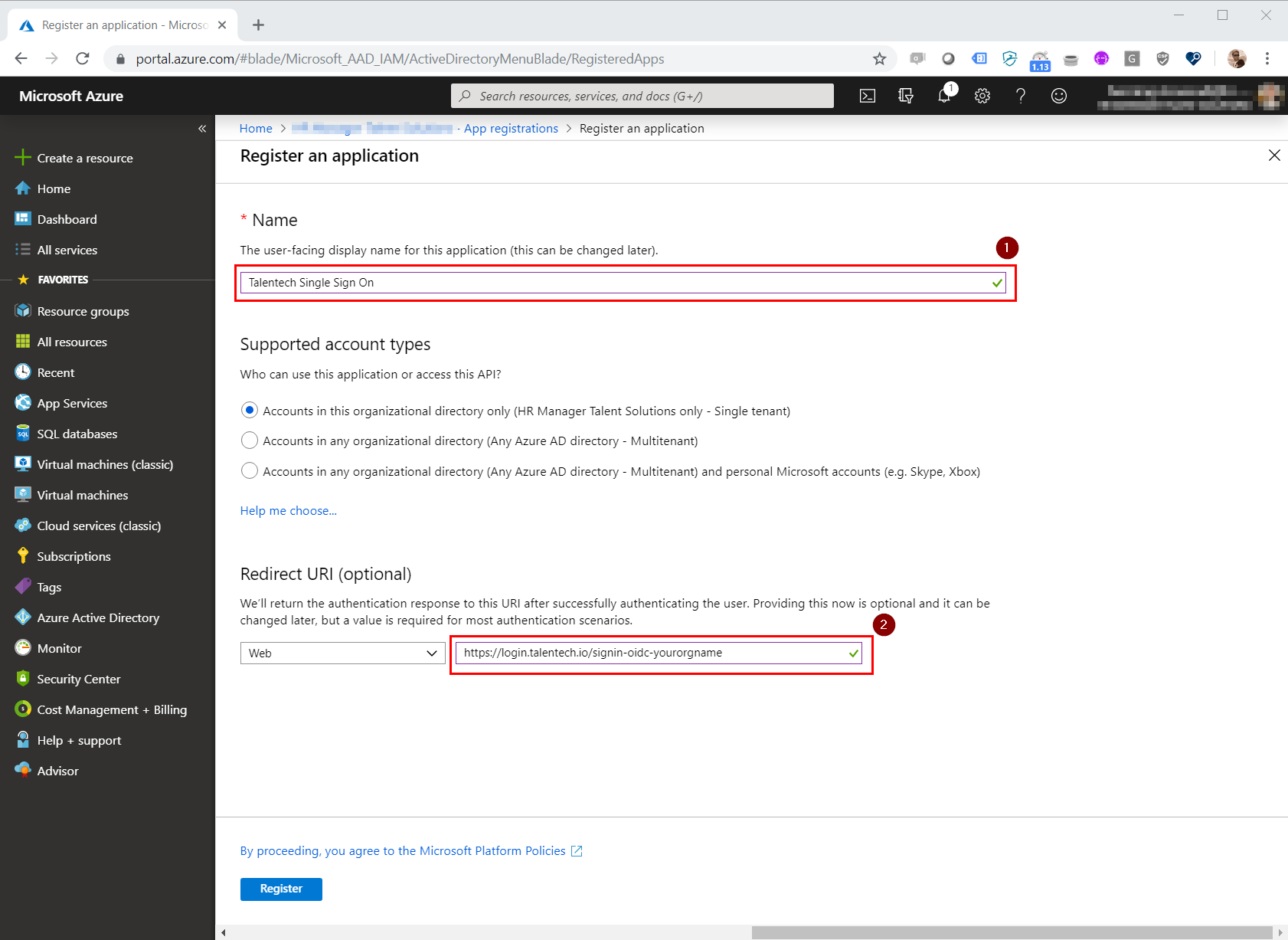
Type in a name of your choice, i.e. "Talentech Single Sign On" (1). You also need to add the redirect URI provided by us. If you haven't recieved it, contact us.
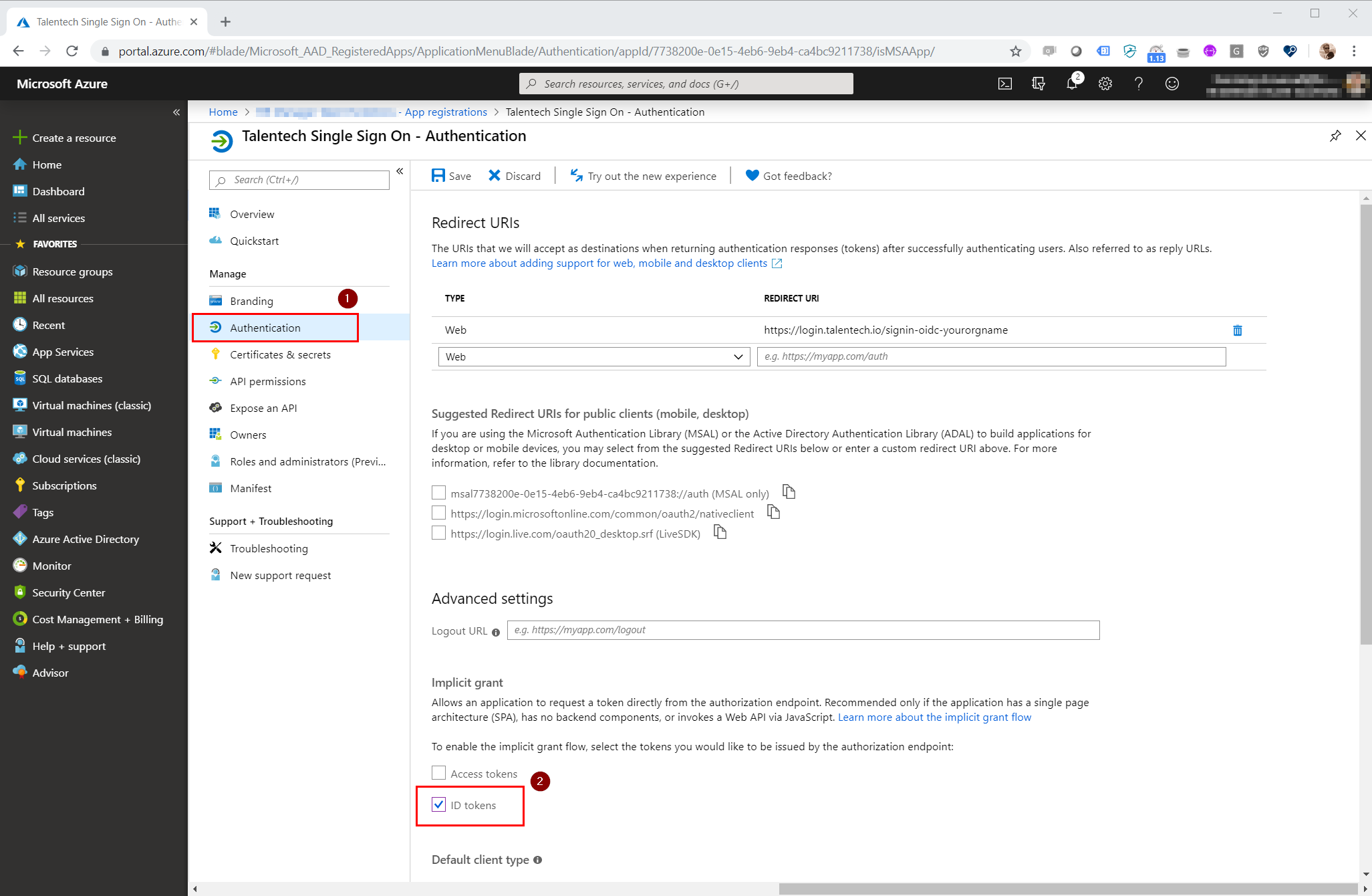
Navigate to "Authentication" (1) and tick the checkbox "ID Tokens" (2)
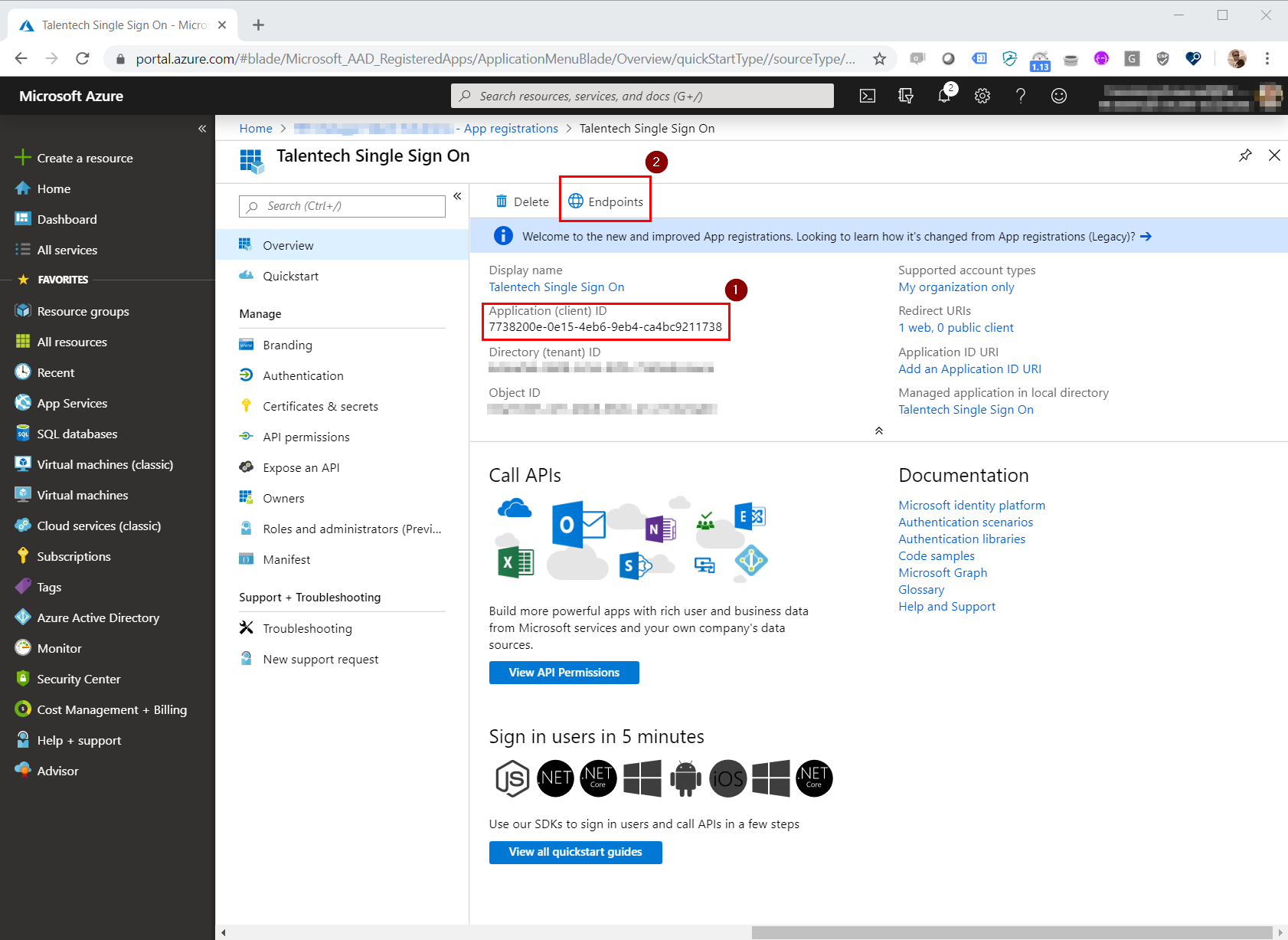
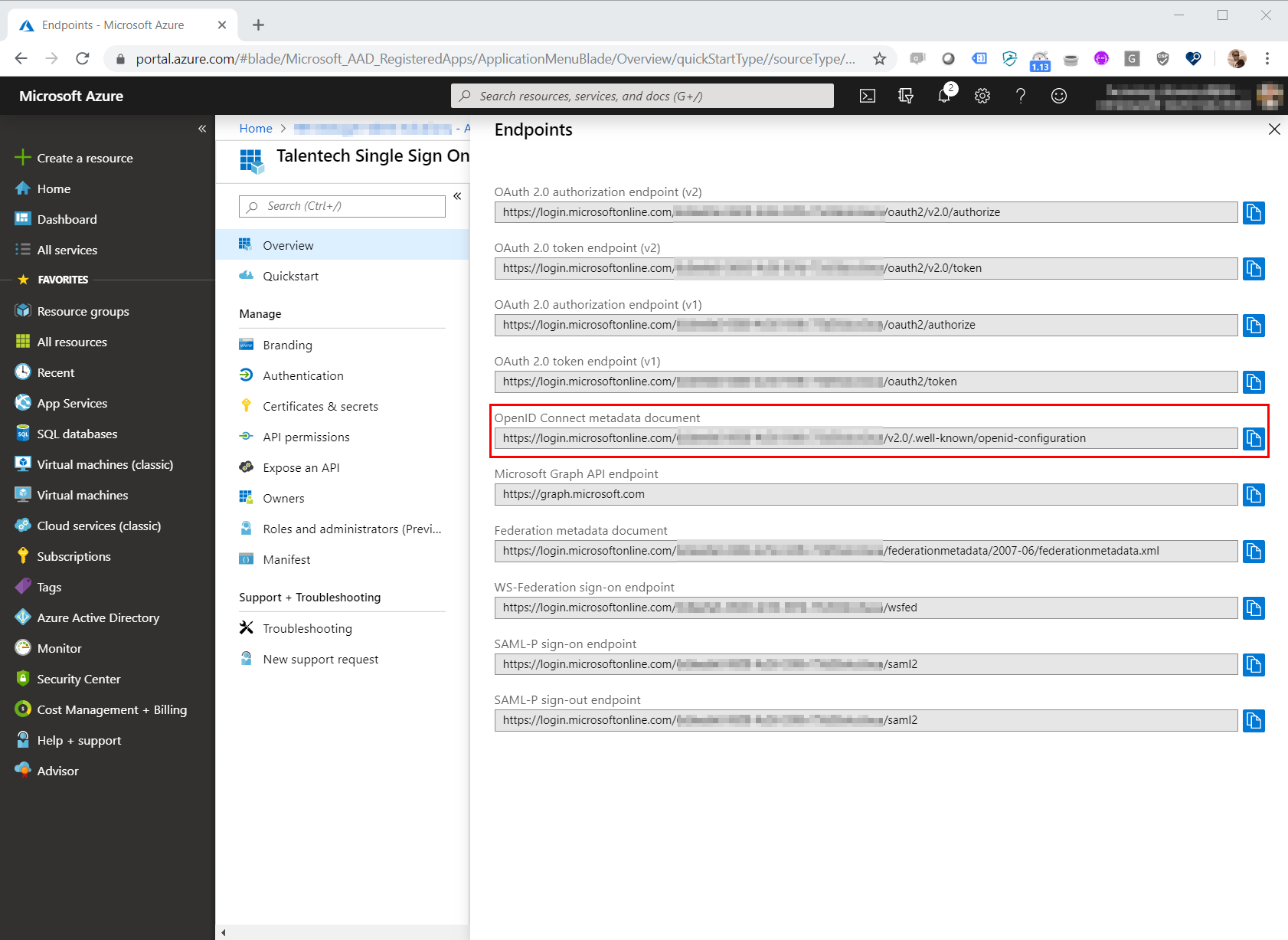
2. Send us your ClientID, ClientSecret and metadata URL
Send us the ClientID, ClientSecret and URL to the OpenID Connect metadata document so we can add this on our side of the setup.
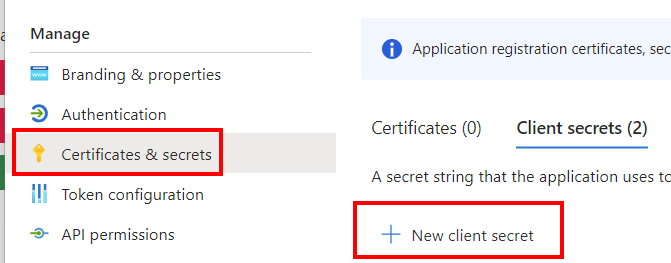
Go to "Certificates & secrets" and create a new secret with 24 month expiration. NB: you must make sure to keep track of the expiration and send us a new secret before the current one expires.
3. Optional: Admin consent for all users
We recommend that you give admin consent for all your users signing in to Talentech ID.
If you do not do this, every user will be asked if they would like to allow Talentech ID to read their basic information when signing in for the first time.
If the user does not give their consent they will not be signed in.
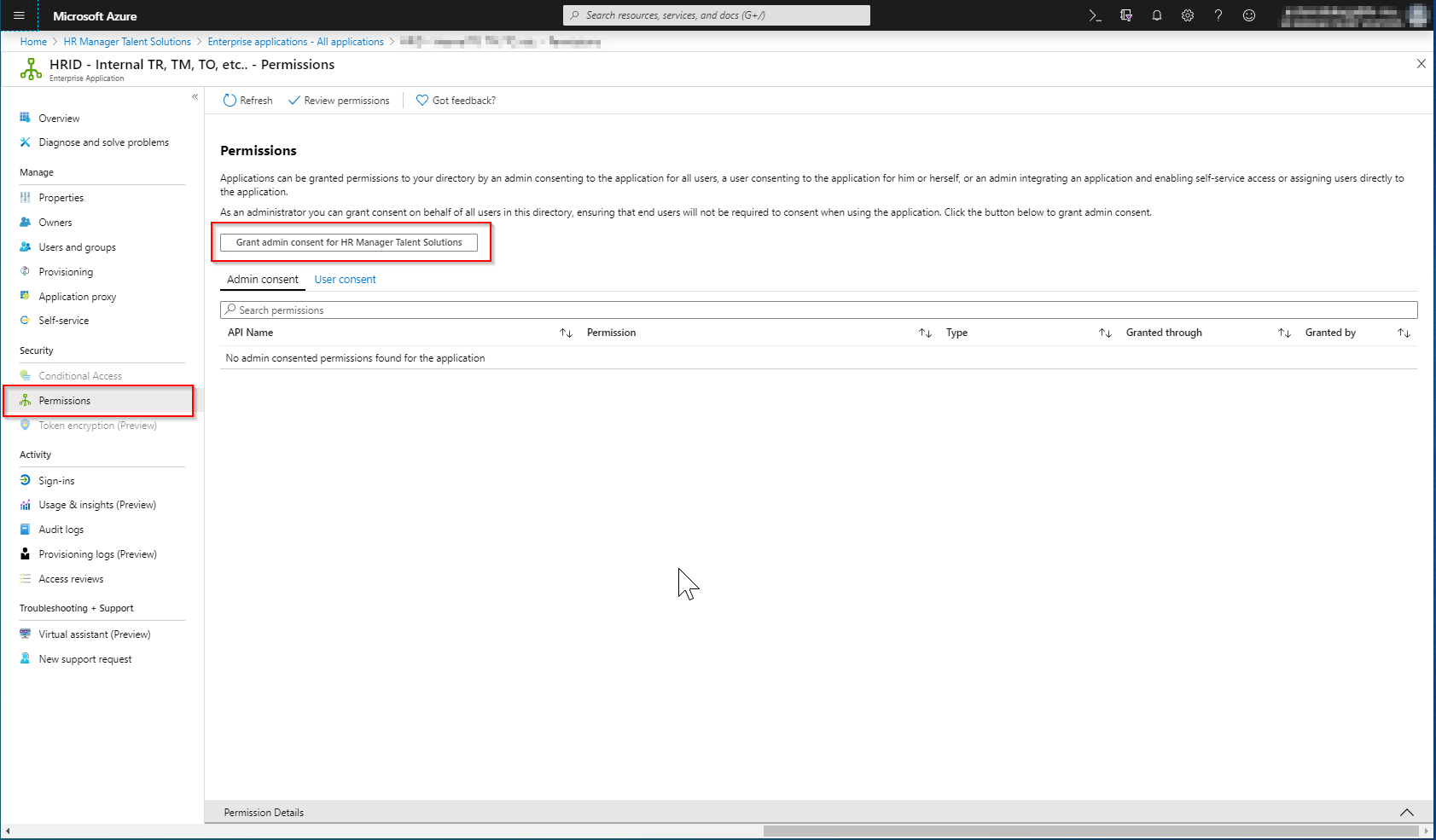
To grant admin consent navigate to "Enterprise Applications" and find your application in the list.
Then navigate to "Permissions" and click "Grant admin consent for.."
4. Optional: Whitelist email addresses
Talentech ID is sending email for password resets and account activations. If you have problems receiving these emails, you should consider whitelisting our email addresses and IP addresses.
Frequently asked questions
- Select Azure Active Directory
- Select Enterprise Applications
- Using the search field, locate the app registration that handles Talentech ID SSO.
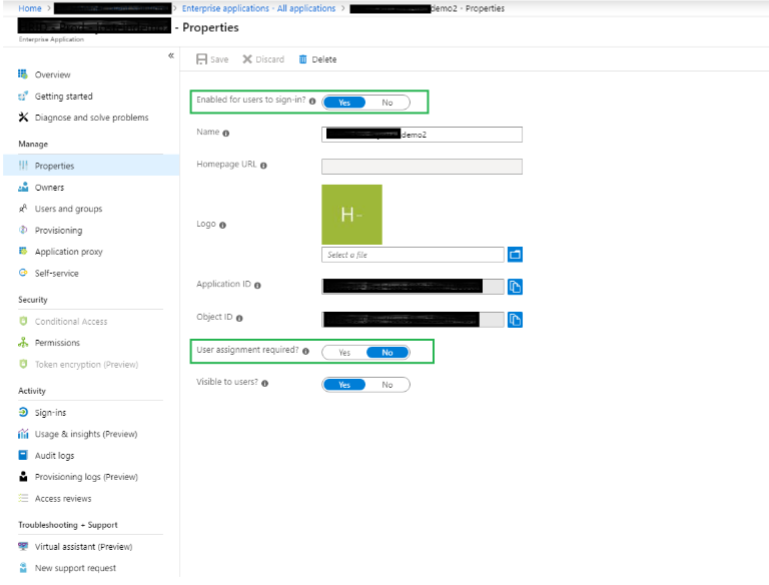
Open the application. - Select the ‘Properties’ menu. Verify that the settings are set as indicated in the green boxes below.
Question
Can I use an Azure AD Enterprise Application instead of an App Registration?
Answer
Yes you can!
Question
Do I need to assign users or groups to the Azure AD Application, or should I allow all users access?
Answer
You can allow all users access to log in via this app because user access is managed in Talent Recruiter, Talent Manager and each corresponding product.
Question
What name do the claim with username need to have?
Answer
To properly map an Azure AD user to a Talentech ID user, the claim with an email address matching the email address in Talentech ID needs to be called [email], [http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress] or [preferred_username]